- There are billions of identities coming online in coming years whether this be refugees and those in developing countries (as referenced heavily at Davos), or devices and things
- These identities all need to be secured, at massive scale…this requires innovative, flexible, future proof identity platforms that can handle this complexity
Position on blockchain (which I need to verify with our internal experts that I am relaying correctly)
- We think it has a lot of potential value, but there’s also a lot noise in the space
- We’re taking a measured approach, have joined the Hyperledger Project to explore more around tracking of valuable assets (IoT, documents, KYC), active policies for authorization that are more dynamic, an immutable record of user consent and its withdrawal
It was truly interesting, but not surprising, to see digital identity become a recurring theme throughout the agenda of this year’s Davos (or, more properly, the 48th World Economic Forum Annual Meeting in Davos). Interesting, because it means that digital identity is now on the agenda for public and private sector strategists at the highest level (and about to become a strategic battleground, in my opinion). For those of who have been saying for some time that the “new economy” is being constrained, and even subverted, by the lack of a practical identity infrastructure in tune with the always-on world, this focus on identity could not have come soon enough. It is not surprising that it has reached the Davos agenda though because anyone who has spent any time trying to construct a vision for future online services must have come to the same broad conclusion: we cannot build services for the post-industrial age using the identity infrastructure of the industrial age. We need a new digital identity infrastructure.
J. C. Smith, CEO of Thompson Reuters: “Digital identity is the building block towards trusted access, authentication and privacy,”
From Digital identity paves way for trusted access, authentication and privacy says CISCO CEO at Davos
Mr. Smith is surely correct. All of the characteristics that we are interested in at the customer level (eg, privacy) can only be delivered through a digital identity layer that forms a fundamental platform for a wide variety of services and in response to a wide variety of use cases. To illustrate just how wide, consider the four use cases that I always put up to test the completeness of any digital identity vision that I am presented with: multiple identities, witness protection, whistleblowing and adult services. Each of these four examples imposes very different demands on digital identity and any practical digital identity system has to cope with all of them in ways that should be determined by society, not by technologists.
“Digital identities and access systems are foundational elements of our shared digital future” said Derek O’Halloran, Head, World Economic Forum System Initiative on Shaping the Future of Digital Economy and Society.
From Digital Identity – Why It Matters and Why It’s Important We Get It Right | World Economic Forum
Mr. O’Halloran is surely correct. I like this framing of issue as shared digital future, because it reinforces the point that digital identity must be shaped by a shared vision that necessarily encompasses some difficult issues. We all understand there are wide cultural differences in how identity is conceptualised and animated. There is no single position on surveillance, to choose an obvious case, that we can use to set all of the requirements. Meeting these varied needs is a really challenge to those of trying to formulate ideas about how to fix the “identity problem”.
Digital identity is relevant in a wide range of situations that require people and entities to prove who they are
From Digital Identity – Why It Matters and Why It’s Important We Get It Right | World Economic Forum
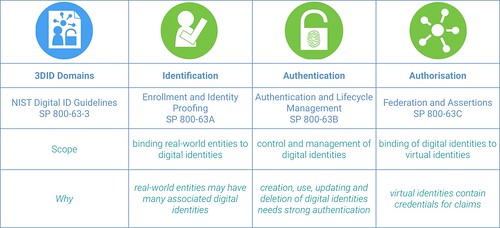
This is, frankly, wrong. And it illustrates just how important it is to build the right conceptual framework around digital identity before we rush to deploy biometrics, bots and blockchains to fix the identity problem referred to above. It is wrong because in almost all of the situations where digital identity is needed in the modern world, it is not to demonstrate who you are but to demonstrate what you are: an employee, a citizen, a subscriber, a member of the club, an adult and so on. One of the most profound elements of the new identity paradigm is to separate the binding of digital identity to real entities from the binding of digital identity to credentials used to enable transactions (and the authentication of the holders of those transactions). You can see this separation clearly in the structure of the draft NIST Digital Identity Guidelines (SP-800-63-3).
 //embedr.flickr.com/assets/client-code.js
//embedr.flickr.com/assets/client-code.js
Generally speaking, transactions need what NIST call here “assertions”. I am over 18, I have this line of credit, I am allowed to drive, I can enter this building, and so on and so forth. These transactions do not need my identity. Far from it: we want to keep personally-identifiable information (PII) out of transactions as much as we can! There is a world of difference, as everyone intuitively knows, between proving that you are over 18 and proving who you are, or giving out your age or your birthdate. This a crucial part of the digital identity post-industrial paradigm, where digital identity forms the bridge between your real identity and your (many) online identities.
OK, so let’s take on board that we have a modern vision of what a modern digital identity infrastructure should do. But now here’s the hard part, and the real challenge to the Davos delegates. How can that vision, and the benefits to society that it can deliver, be extended to everyone. Everyone. Even people who have no identity all at the moment.
“We estimate it will take $12 billion to achieve identification for all. The World Bank will secure over $750 million investments in ID-related projects in the next three years and we will strive to mobilize more financing from other sources,” said Kristalina Georgieva, Chief Executive Officer, World Bank and co-chair of the Identification for Development (ID4D) High-Level Advisory Council
From Digital Identity – Why It Matters and Why It’s Important We Get It Right > Press releases | World Economic Forum
Wow. That’s a lot of money in anyone’s language and perhaps it is one of the reasons why there has been little progress so far. Even if we can agree on shared vision, it is a huge enterprise to deliver it and it must be obvious that given the scale of the enterprise (after all, we are talking about billions of identities here) it can only be achieved by bringing together government, NGO and private sector initiatives. Now, the good news is that the first steps in this direction have been taken, with a wide variety of such organisations committing to tackling the growing global problem.
The UNHCR, World Bank, World Food Programme, Consumers International, Omidyar Network, the Linux Foundation, FIDO Alliance, GSMA, Hyperledger, ID2020, Open Identity Exchange, Sovrin Foundation, World Identity Network, Accenture, Barclays, Deutsche Bank, Mastercard, Microsoft, Sedicii and Visa have announced their commitment to strengthen collective action on [digital identity].
From Digital identity – it matters that we get it right
It is interesting to note the new technology angle, with organisations such as Hyperledger and Sovrin, appearing in this list. There was a lot of discussion of how “the blockchain” could help although it was at high level and a long way from practical deployment. I strongly agree with the idea that we not only need to get digital identity right but also need to deliver it to everybody. Whether the best way to achieve this is using cryptocurrency or a database, individuals or institutions, is up for debate. (In particular, I feel that that the idea that blockchain will solve the problem by doing away with institutions needs to be examined sceptically.) Still, as the technology evolves, so will that debate. ForgeRock has joined to Hyperledger Project to be a constructive part in that debate and bring experience of large-scale deployments to the table. If the disparate organisations and perspectives going into that debate are going to make progress, they need to make a strong start, so I’d like to make a practical suggestion of positive 1-2-3 steps to hit the ground running!
-
Develop a common framework for digital identity to facilitate conversation between the stakeholders and to construct a paradigm for the new online age. I’m not smart enough to know what this should be, but I do think the “Three Domain Identity” (3DID) that I developed with my colleagues at Consult Hyperion is a constructive contribution to a discussion about that model.
-
Develop a common set of requirements that can be agreed (and I do not underestimate how difficult this will be) between governments, NGOs, IT suppliers, academics, human rights lawyers and others. They’ll have to be simple and clear!
-
Develop narratives to show, demonstrate and inspire around implementations of the digital identity model meeting those agreed requirements.
Whether a revolution that bypasses institutions or a mechanism for radical transparency in existing institutions, there was blockchain in the air at Davos. Even if you are sceptical about blockchain as a solution to any or all of the world’s identity problems, it does seem to me that there are a great many practical issues — ranging from the management of keys to the discoverability of identities, from the standardisation of attributes to the protection of personal data — that might be catalysed through the use of the new technology. Whether we are trying to bringing efficiency to government operations, reduce fraud in commercial transactions or protect the human rights of refugees, working together to co-evolve practical ways to deliver on the shared vision can only be a good thing.